Implementing Aruba IntroSpect: HPE2-W05
Want to pass your Implementing Aruba IntroSpect HPE2-W05 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: HP
- Exam Code: HPE2-W05
- Exam Name: Implementing Aruba IntroSpect
- Certifications: HP Certifications
- Total Questions: 115 Q&As( View Details)
- Updated on: Jan 30, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
HP HPE2-W05 Last Month Results
Free HPE2-W05 Exam Questions in PDF Format
Related HP Certifications Exams
HPE2-W05 Online Practice Questions and Answers
Questions 1
Refer to the exhibit.
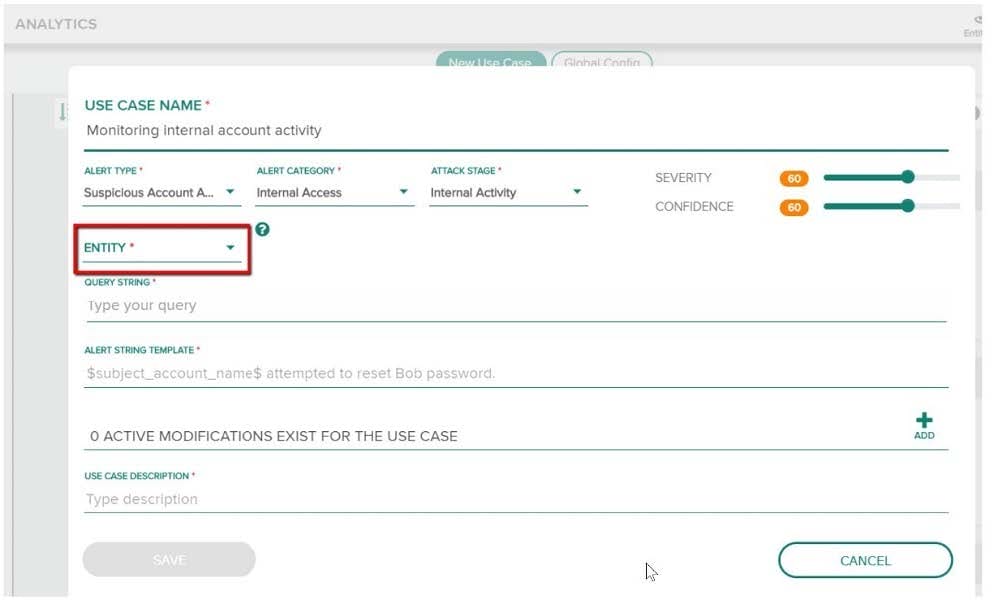
You have been assigned a task to monitor, analyze, and find those entities who are trying to access internal resources without having valid user credentials. You are creating an AD-based use case to look for this activity. Could you use this entity type to accomplish this? (Host name.)
A. Yes
B. No
Questions 2
Your company has found some suspicious conversations for some internal users. The security team suspects those users are communicating with entities in other countries. You have been assigned the task of identifying those users who are either uploading or downloading files from servers in other countries. Is this the best way to visualize conversations of suspected users in this scenario? (Visualizing conversation graphs.)
A. Yes
B. No
Questions 3
While investigating alerts you notice a user entity has triggered a historical alert for Large Internal Data Download. While investigating the alert, you notice that the download came from a different device than normal for the user. Based on these conditions, is this a possible cause? (This is a classic user account take over pattern.)
A. Yes
B. No
Reviews
-
A very helpful study material, I have passed the exam with the help of this dumps. So i will introduce this dumps to other friend.
-
Thanks for your help I pass my exam yesterday. Although I did not get a very high score but never mind. Thanks.
-
Valid material !! I will continue using this material and introduced it to other friend. Good thing should be shared with friend.
-
Thanks for your help. I passed my exam yesterday with the full points! Great job.
-
yes, i passed the exam in the morning, thanks for this study material. Recommend.
-
A very good study material, i just used one month and i passed the exam yesterday. So you can trust on it.
-
the content update quickly, there are many new questions in this dumps. thanks very much.
-
Dump is valid. Thanks for all.
-
there are 4 questions different. these are about t.shoot questions. but the rest is ok for pass. Good dumps.
-
This dumps is very very valid. I passed this week with a satisfied score. ALL questions were from this file.


 Printable PDF
Printable PDF