GIAC Certified Enterprise Defender (GCED): GCED
Want to pass your GIAC Certified Enterprise Defender (GCED) GCED exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: GIAC
- Exam Code: GCED
- Exam Name: GIAC Certified Enterprise Defender (GCED)
- Certifications: GIAC Certifications
- Total Questions: 88 Q&As( View Details)
- Updated on: Mar 03, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
GIAC GCED Last Month Results
Free GCED Exam Questions in PDF Format
Related GIAC Certifications Exams
GCED Online Practice Questions and Answers
Questions 1
Analyze the screenshot below. Which of the following attacks can be mitigated by these configuration settings?
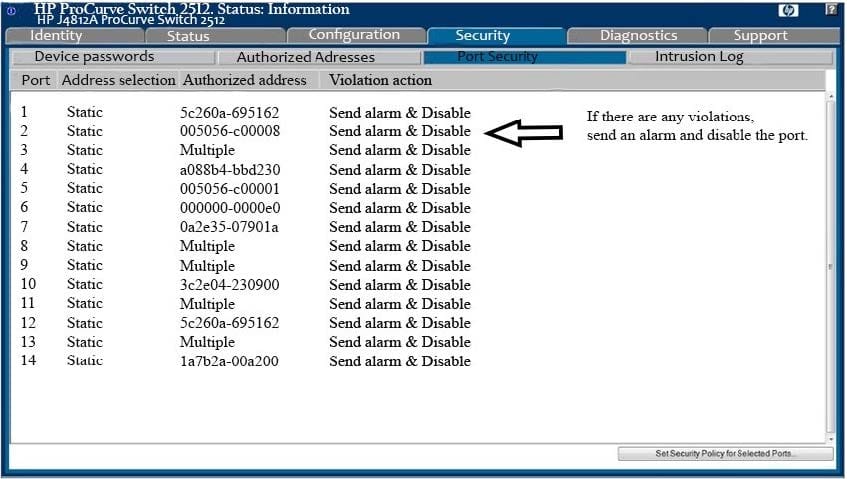
A. A Denial-of-Service attack using network broadcasts
B. A Replay attack
C. An IP masquerading attack
D. A MAC Flood attack
Questions 2
Which of the following attacks would use ".." notation as part of a web request to access restricted files and directories, and possibly execute code on the web server?
A. URL directory
B. HTTP header attack
C. SQL injection
D. IDS evasion
E. Cross site scripting
Questions 3
The security team wants to detect connections that can compromise credentials by sending them in plaintext across the wire. Which of the following rules should they enable on their IDS sensor?
A. alert tcp any 22 < > any 22 (msg:SSH connection; class type:misc-attack;sid: 122:rev:1;)
B. alert tcp any any < > any 6000: (msg:X-Windows session; flow:from_server,established;nocase;classtype:misc-attack;sid:101;rev:1;)
C. alert tcp any 23 < > any 23 (msg:Telnet shell; class type:misc-attack;sid:100; rev:1;)
D. alert udp any any < > any 5060 (msg:VOIP message; classtype:misc-attack;sid:113; rev:2;)
Reviews
-
All this dumps are very good, i just did this one and took part in my exam. i really don't believe myself that i have got so high score. Thanks for their dumps.
-
Many questions are from the dumps but few question changed. Need to be attention.
-
Got 950 pass monday, almost all questions from this dumps.. So its VALID!!
-
Very effective study material.I just passed my exam. As long as you studied this material careful, you will pass the exam with high score. Recommend.
-
At first, i don’t think i can pass the exam. But when i used this dumps, i felt more confident to pass the exam. It is not out of my expectation, i passed the exam with the full score because I met many same question that i have done in this dumps. Thanks this dumps, it is useful.
-
I passed the exam with perfect score. I'm so happy now. Thanks for my friends introduction, thanks for this dumps.
-
Passed with unexpected score. A big surprise. Thanks very much.
-
Recommend this dumps to you strongly, really useful and convenient.
-
I have cleared that i passed the exam today. Thanks so much.
-
The new questions in the exam are not the new questions for me because I have met them when I used this material . So there is no doubt that I have passed the exam with high score. Recommend this material strongly.


 Printable PDF
Printable PDF