GIAC Critical Controls Certification (GCCC): GCCC
Want to pass your GIAC Critical Controls Certification (GCCC) GCCC exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: GIAC
- Exam Code: GCCC
- Exam Name: GIAC Critical Controls Certification (GCCC)
- Certifications: GIAC Certifications
- Total Questions: 93 Q&As( View Details)
- Updated on:
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
GIAC GCCC Last Month Results
Free GCCC Exam Questions in PDF Format
Related GIAC Certifications Exams
GCCC Online Practice Questions and Answers
Questions 1
To effectively implement the Data Protection CIS Control, which task needs to be implemented first?
A. The organization's proprietary data needs to be encrypted
B. Employees need to be notified that proprietary data should be protected
C. The organization's proprietary data needs to be identified
D. Appropriate file content matching needs to be configured
Questions 2
What is a zero-day attack?
A. An attack that has a known attack signature but no available patch
B. An attack that utilizes a vulnerability unknown to the software developer
C. An attack that deploys at the end of a countdown sequence
D. An attack that is launched the day the patch is released
Questions 3
DHCP logging output in the screenshot would be used for which of the following?
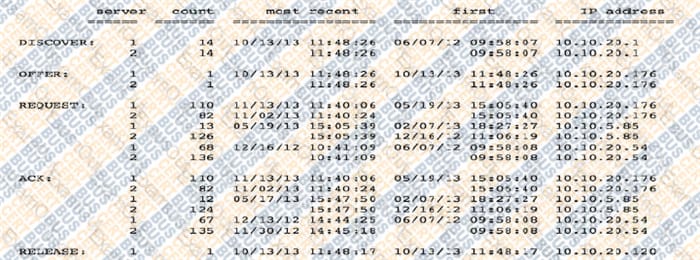
A. Enforcing port-based network access control to prevent unauthorized devices on the network.
B. Identifying new connections to maintain an up-to-date inventory of devices on the network.
C. Detecting malicious activity by compromised or unauthorized devices on the network.
D. Providing ping sweep results to identify live network hosts for vulnerability scanning.
Reviews
-
i'm very happy that i passed the exam successfully. Recommend.
-
this file is so much valid, i passed the exam successfully. thanks for my friend introduce this dumps to me.
-
Very good study material, I just passed my exam with the help of it. Good luck to you.
-
I think it is useful and convenient, you can use your spare time do the questions in this dumps if you are busy with your work. And this dumps is enough for your exam. Just try on and you will achieve high score in the exam. Just like me, Good luck to you.
-
I love this dumps. It really helpful and convenient. Recommend strongly.
-
Yesterday, I passed the exam with unexpected score with the help of this dumps. Thanks for this dumps.Recommend strongly.
-
Thanks god and thank you all. 100% valid. all the other questions are included in this file.
-
Their dumps is a very recent update. All the new questions are there! Recommend.
-
I passed my exam this morning. I prepared with this dumps two weeks ago. This dumps is very valid. All the questions were in my exam. I still got 2 new questions but luckily they are easy for me. Thanks for your help. I will recommend you to everyone I know.
-
took the exams yesterday and passed. I was very scared at first because the labs came in first so I was spending like 10 to 13mins so I started rushing after the first three labs thinking that I will have more labs. I ended up finishing the exam in an hour..d dumps are valid. I tink there is a new lab. good success


 Printable PDF
Printable PDF