EC-Council Certified Security Analyst (ECSA) v8: ECSAv8
Want to pass your EC-Council Certified Security Analyst (ECSA) v8 ECSAv8 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: EC-COUNCIL
- Exam Code: ECSAv8
- Exam Name: EC-Council Certified Security Analyst (ECSA) v8
- Certifications: EC-COUNCIL Certifications
- Total Questions: 200 Q&As
- Updated on: Jan 12, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
EC-COUNCIL ECSAv8 Last Month Results
Free ECSAv8 Exam Questions in PDF Format
Related EC-COUNCIL Certifications Exams
ECSAv8 Online Practice Questions and Answers
Questions 1
This is a group of people hired to give details of the vulnerabilities present in the system found after a penetration test. They are elite and extremely competent penetration testers and intrusion analysts. This team prepares a report on the vulnerabilities in the system, attack methods, and how to defend against them.

What is this team called?
A. Blue team
B. Tiger team
C. Gorilla team
D. Lion team
Questions 2
Phishing is typically carried out by email spoofing or instant messaging and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one.
Phishing is an example of social engineering techniques used to deceive users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.
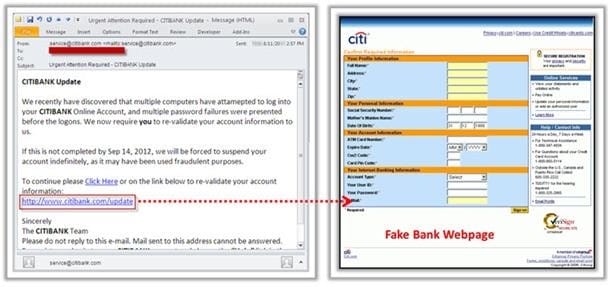
What characteristics do phishing messages often have that may make them identifiable?
A. Invalid email signatures or contact information
B. Suspiciously good grammar and capitalization
C. They trigger warning pop-ups
D. Suspicious attachments
Questions 3
An automated electronic mail message from a mail system which indicates that the user does not exist on that server is called as?
A. SMTP Queue Bouncing
B. SMTP Message Bouncing
C. SMTP Server Bouncing
D. SMTP Mail Bouncing
Reviews
-
Valid. Passed Today.....So happy, I will recommend it to my friends.
-
Great dumps! I have passed the exam by using this dumps only half a month. I will share with my friend.
-
Valid. Pass with 9XX. Good Luck!!!
-
This dumps is still very valid, I have cleared the written exams passed today. Recommend.
-
It is out of my expectation that there will be so valid dumps. Thanks for all of you.
-
At first, i don’t think i can pass the exam. But when i used this dumps, i felt more confident to pass the exam. It is not out of my expectation, i passed the exam with the full score because I met many same question that i have done in this dumps. Thanks this dumps, it is useful.
-
I have passed the exam with their dumps. Thanks a million!
-
Valid dumps. I hope all my friend will pass the exam, so I will introduce this dumps to them.Good luck to them and you.
-
today all the question are from this dumps, so i passed the exam without doubt. thanks for it. Recommend.
-
This dumps is still valid. Just took my CCNA today and passed it. Every question i got on the test was in the dumps.


 Printable PDF
Printable PDF