EC-Council Certified Security Analyst (ECSA) v10: ECSAV10
Want to pass your EC-Council Certified Security Analyst (ECSA) v10 ECSAV10 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: EC-COUNCIL
- Exam Code: ECSAV10
- Exam Name: EC-Council Certified Security Analyst (ECSA) v10
- Certifications: EC-COUNCIL Certifications
- Total Questions: 354 Q&As( View Details)
- Updated on: Jan 12, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
EC-COUNCIL ECSAV10 Last Month Results
Free ECSAV10 Exam Questions in PDF Format
Related EC-COUNCIL Certifications Exams
ECSAV10 Online Practice Questions and Answers
Questions 1
Richard is working on a web app pen testing assignment for one of his clients. After preliminary
information, gathering and vulnerability scanning Richard runs the SQLMAP tool to extract the database
information.
Which of the following commands will give Richard an output as shown in the screenshot?
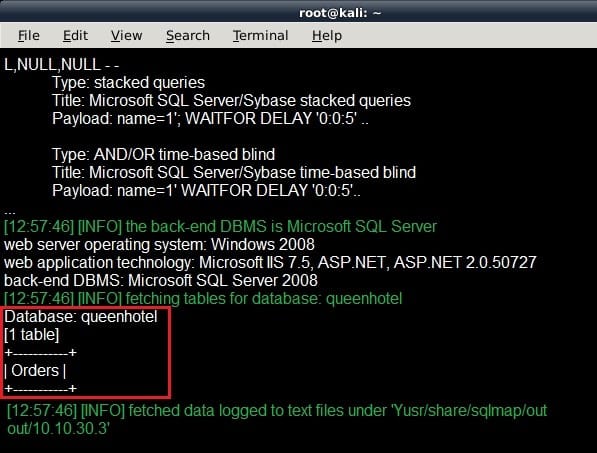
A. sqlmap –url http://quennhotel.com/about.aspx?name=1 –D queenhotel --tables
B. sqlmap –url http://quennhotel.com/about.aspx?name=1 –dbs
C. sqlmap –url http://quennhotel.com/about.aspx?name=1 –D queenhotel –T --columns
D. sqlmap –url http://quennhotel.com/about.aspx?name=1 –database queenhotel –tables
Questions 2
A team of cyber criminals in Germany has sent malware-based emails to workers of a fast-food center which is having multiple outlets spread geographically. When any of the employees click on the malicious email, it will give backdoor access to the point of sale (POS) systems located at various outlets. After gaining access to the POS systems, the criminals will be able to obtain credit card details of the fast-food center's customers. In the above scenario, identify the type of attack being performed on the fast-food center?
A. Phishing
B. Vishing
C. Tailgating
D. Dumpster diving
Questions 3
What is the objective of the following bash script?
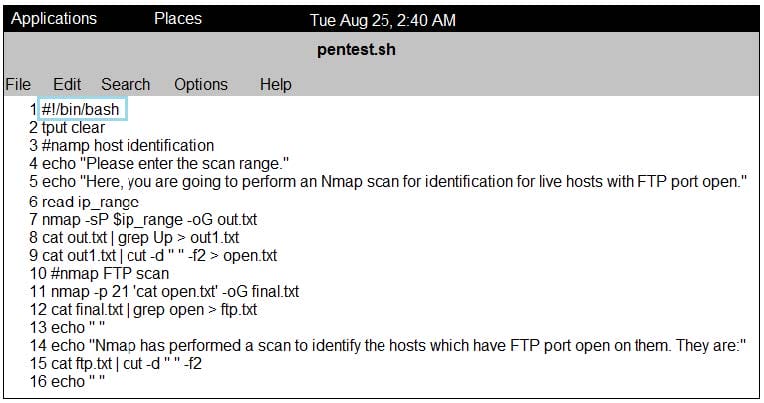
A. It gives a list of IP addresses that have an FTP port open
B. It tries to connect to FTP port on a target machine C. It checks if a target host has the FTP port open and quits
D. It checks if an FTP port on a target machine is vulnerable to arracks
Reviews
-
Valid. All questions from the exam, few questions have the different order. So please be careful in the exam,
-
passed the exam today. all the question from this dumps,so you can trust on it.
-
Very useful study material, thanks the help of this dumps .
-
I passed my exam this morning. I prepared with this dumps two weeks ago. This dumps is very valid. All the questions were in my exam. I still got 2 new questions but luckily they are easy for me. Thanks for your help. I will recommend you to everyone I know.
-
I have tested yet. I prepared my exam only with their materials. Recommend.
-
This dumps was introduced by my good friend several month ago. At first, I don't think it will help me a lot. But when I found many new questions that I never found from other study materials, i begun to pay more attention on this dumps. At last, I only used this dumps for preparing my exam. A moment ago, i have cleared that i passed the exam with almost full score. Thanks for this dumps, i will recommend to others just as my friend do.
-
Test engine works fine. Pass my exam. Thank you.
-
This study material is very useful and effective, if you have not much time to prepare for your exam, this study material is your best choice.
-
I have passed the exam with their dumps. Thanks a million!
-
I really felt surprised that i would pass the exam with so high score by using this dumps. I will share this good study material with my friends.


 Printable PDF
Printable PDF