Computer Hacking Forensic Investigator Exam: EC1-349
Want to pass your Computer Hacking Forensic Investigator Exam EC1-349 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: EC-COUNCIL
- Exam Code: EC1-349
- Exam Name: Computer Hacking Forensic Investigator Exam
- Certifications: CHFI
- Total Questions: 486 Q&As
- Updated on: Dec 16, 2024
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
EC-COUNCIL EC1-349 Last Month Results
Free EC1-349 Exam Questions in PDF Format
Related CHFI Exams
EC1-349 Online Practice Questions and Answers
Questions 1
You are conducting an investigation of fraudulent claims in an insurance company that involves complex text searches through large numbers of documents. Which of the following tools would allow you to quickly and efficiently search for a string within a file on the bitmap image of the target computer?
A. Stringsearch
B. grep
C. dir
D. vim
Questions 2
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
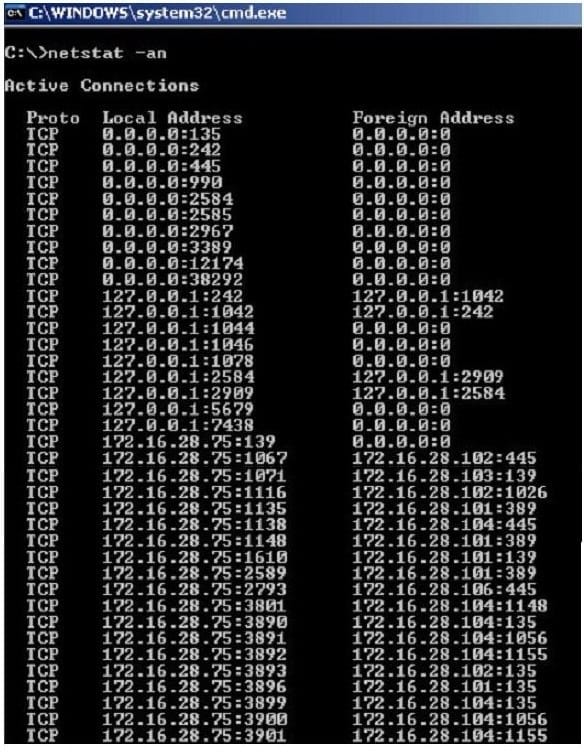
He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
A. Those connections are established
B. Those connections are in listening mode
C. Those connections are in closed/waiting mode
D. Those connections are in timed out/waiting mode
Questions 3
Email archiving is a systematic approach to save and protect the data contained in emails so that it can tie easily accessed at a later date.
A. True
B. False
Reviews
-
passed, passed, passed .thanks a lot
-
this dumps is valid. All questions that I met in the exam are from this dumps !!!
-
I studied this material carefully and took every question seriously. At last, I passed the exam with high score. Prepare well and study much more.
-
This study material is very useful and effective, if you have not much time to prepare for your exam, this study material is your best choice.
-
I passed. Good luck to you.
-
Thanks for your help. I passed my exam yesterday with a high score. I think you have the great dumps. all my questions are from your materials. I'm very happy with that. Thanks.
-
I used it,I passed. I found same questions..but it's not the same orderl, be careful.
-
Many questions are from the dumps but few question changed. Need to be attention.
-
I pass today . In my opinion,this dumps is enough to pass exam. Good luck to you.
-
I pass my exam with a pretty score. The dumps are good and all the answers are correct. If you want to pass , you can use this dumps.


 Printable PDF
Printable PDF