Computer Hacking Forensic Investigator: EC0-349
Want to pass your Computer Hacking Forensic Investigator EC0-349 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: EC-COUNCIL
- Exam Code: EC0-349
- Exam Name: Computer Hacking Forensic Investigator
- Certifications: EC-COUNCIL Certifications
- Total Questions: 304 Q&As( View Details)
- Updated on: Jan 14, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
EC-COUNCIL EC0-349 Last Month Results
Free EC0-349 Exam Questions in PDF Format
Related EC-COUNCIL Certifications Exams
EC0-349 Online Practice Questions and Answers
Questions 1
A computer forensics investigator is inspecting the firewall logs for a large financial institution that has employees working 24 hours a day, 7 days a week.
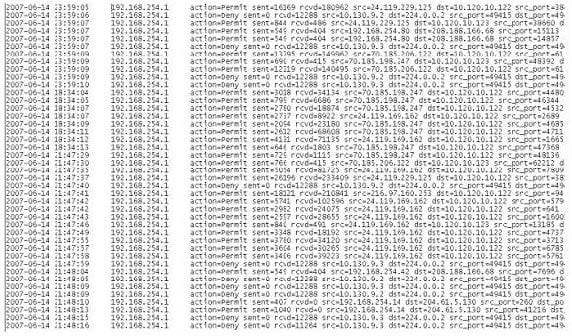
What can the investigator infer from the screenshot seen below?
A. A smurf attack has been attempted
B. A denial of service has been attempted
C. Network intrusion has occurred
D. Buffer overflow attempt on the firewall.
Questions 2
When obtaining a warrant, it is important to:
A. particularlydescribe the place to be searched and particularly describe the items to be seized
B. generallydescribe the place to be searched and particularly describe the items to be seized
C. generallydescribe the place to be searched and generally describe the items to be seized
D. particularlydescribe the place to be searched and generally describe the items to be seized
Questions 3
You are working as an independent computer forensics investigator and receive a call from a systems administrator for a local school system requesting your assistance. One of the students at the local high school is suspected of downloading inappropriate images from the Internet to a PC in the Computer lab. When you arrive at the school, the systems administrator hands you a hard drive and tells you that he made a simple backup copy of the hard drive in the PC and put it on this drive and requests that you examine that drive for evidence of the suspected images. You inform him that a simple backup copy will not provide deleted files or recover file fragments.
What type of copy do you need to make to ensure that the evidence found is complete and admissible in future proceedings?
A. Bit-stream Copy
B. Robust Copy
C. Full backup Copy
D. Incremental Backup Copy
Reviews
-
This dumps is very valid, and i have passed the exam perfectly. Thanks very much, I will continue using it.
-
I pass today . In my opinion,this dumps is enough to pass exam. Good luck to you.
-
I'm so glad that I have chosen you as my assistant with my exam. I passed my exam. Full scored. I will recommend to friends.
-
Now, i have finished my exam. I really appreciate for the help of this dumps. Thanks very much.
-
I passed. Good luck to you.
-
This dumps is useful and helpful, I also introduced it to my good friend. Now, we passed the exam together. Thanks for this dumps.
-
Valid study material! Go get it now!!!
-
Simulation still valid..passed with a score of 917 :-D
-
Yeah , Get 869/1000 score, this dumps still valid 100% but the some os answer is not correct.
-
Passed today with full score. I prepare only with this dumps. Valid.


 Printable PDF
Printable PDF