
 Printable PDF
Printable PDF
CompTIA SecurityX: CAS-005
Want to pass your CompTIA SecurityX CAS-005 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: CompTIA
- Exam Code: CAS-005
- Exam Name: CompTIA SecurityX
- Certifications: CompTIA Certifications
- Total Questions: 214 Q&As( View Details)
- Updated on: Feb 16, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
CompTIA CAS-005 Last Month Results
Related CompTIA Certifications Exams
CAS-005 Online Practice Questions and Answers
Questions 1
A security analyst is reviewing the following log:
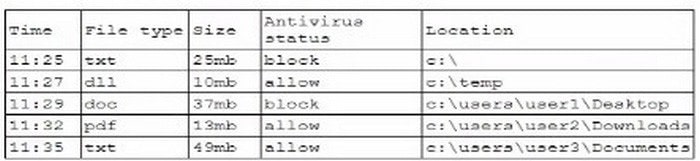
Which of the following possible events should the security analyst investigate further?
A. A macro that was prevented from running
B. A text file containing passwords that were leaked
C. A malicious file that was run in this environment
D. A PDF that exposed sensitive information improperly
Questions 2
An application engineer is using the Swagger framework to leverage REST APIs to authenticate endpoints. The engineer is receiving HTTP 403 responses. Which of the following should the engineer do to correct this issue? (Choose two.)
A. Obtain a security token.
B. Obtain a public key.
C. Leverage Kerberos for authentication
D. Leverage OAuth for authentication.
E. Leverage LDAP for authentication.
F. Obtain a hash value.
Questions 3
A common industrial protocol has the following characteristics:
1.
Provides for no authentication/security
2.
Is often implemented in a client/server relationship
3.
Is implemented as either RTU or TCP/IP
Which of the following is being described?
A. Profinet
B. Modbus
C. Zigbee
D. Z-Wave
Reviews
-
i really love this dumps, update quickly and content completely. it is enough for my exam. Recommend.
-
Thanks for the help of this dumps, i achieved the full score in the exam. I will share this dumps with my good friends.
-
Thanks god and thank you all. 100% valid. all the other questions are included in this file.
-
A very helpful study material, I have passed the exam with the help of this dumps. So i will introduce this dumps to other friend.
-
thanks god and thank you all. 100% valid. you can trust on it.
-
Thanks for your help. I passed my exam yesterday with a high score. I think you have the great dumps. all my questions are from your materials. I'm very happy with that. Thanks.
-
I passed my exam this morning. I only used their braindumps This dumps is valid. I suggest you to prepare your exams with this. Very recommend.
-
I appreciated this dumps not only because it helped me pass the exam, but also because I learned much knowledge and skills. Thanks very much.
-
This study material is very useful and effective, if you have not much time to prepare for your exam, this study material is your best choice.
-
Passed today with full score. I prepare only with this dumps. Valid.
