AWS Certified Security - Specialty (SCS-C01): SCS-C01
Want to pass your AWS Certified Security - Specialty (SCS-C01) SCS-C01 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: Amazon
- Exam Code: SCS-C01
- Exam Name: AWS Certified Security - Specialty (SCS-C01)
- Certifications: Amazon Certifications
- Total Questions: 733 Q&As( View Details)
- Updated on: Mar 09, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
Amazon SCS-C01 Last Month Results
Free SCS-C01 Exam Questions in PDF Format
Related Amazon Certifications Exams
SCS-C01 Online Practice Questions and Answers
Questions 1
A company has set up the following structure to ensure that their S3 buckets always have logging enabled
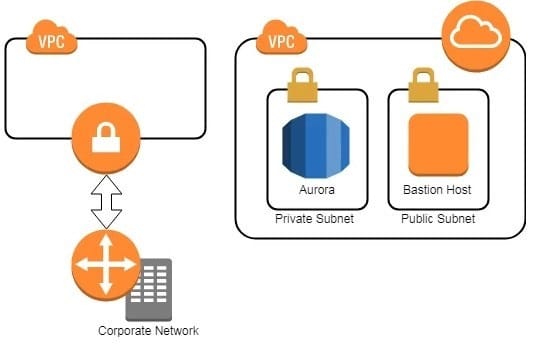
If there are any changes to the configuration to an S3 bucket, a config rule gets checked. If logging is disabled , then Lambda function is invoked. This Lambda function will again enable logging on the S3 bucket. Now there is an issue being encoutered with the entire flow. You have verified that the Lambda function is being invoked. But when logging is disabled for the bucket, the lambda function does not enable it again. Which of the following could be an issue
Please select:
A. The AWS Config rule is not configured properly
B. The AWS Lambda function does not have appropriate permissions for the bucket
C. The AWS Lambda function should use Node.js instead of python.
D. You need to also use the API gateway to invoke the lambda function
Questions 2
An organizational must establish the ability to delete an AWS KMS Customer Master Key (CMK) within a 24-hour timeframe to keep it from being used for encrypt or decrypt operations.
Which of the following actions will address this requirement?
A. Manually rotate a key within KMS to create a new CMK immediately
B. Use the KMS import key functionality to execute a delete key operation
C. Use the schedule key deletion function within KMS to specify the minimum wait period for deletion
D. Change the KMS CMK alias to immediately prevent any services from using the CMK.
Questions 3
A company has two VPCs in the same AWS Region and in the same AWS account Each VPC uses a CIDR block that does not overlap with the CIDR block of the other VPC One VPC contains AWS Lambda functions that run inside a subnet that accesses the internet through a NAT gateway. The Lambda functions require access to a publicly accessible Amazon Aurora MySQL database that is running in the other VPC
A security engineer determines that the Aurora database uses a security group rule that allows connections from the NAT gateway IP address that the Lambda functions use. The company's security policy states that no database should be publicly accessible.
What is the MOST secure way that the security engineer can provide the Lambda functions with access to the Aurora database?
A. Move the Aurora database into a private subnet that has no internet access routes in the database's current VPC Configure the Lambda functions to use the Aurora database's new private IP address to access the database Configure the Aurora databases security group to allow access from the private IP addresses of the Lambda functions
B. Establish a VPC endpoint between the two VPCs in the Aurora database's VPC configure a service VPC endpoint for Amazon RDS In the Lambda functions' VPC. configure an interface VPC endpoint that uses the service endpoint in the Aurora database's VPC Configure the service endpoint to allow connections from the Lambda functions.
C. Establish an AWS Direct Connect interface between the VPCs Configure the Lambda functions to use a new route table that accesses the Aurora database through the Direct Connect interface Configure the Aurora database's security group to allow access from the Direct Connect interface IP address
D. Move the Lambda functions into a public subnet in their VPC Move the Aurora database into a private subnet in its VPC Configure the Lambda functions to use the Aurora database's new private IP address to access the database Configure the Aurora database to allow access from the public IP addresses of the Lambda functions
Reviews
-
passed the exam today. all the question from this dumps,so you can trust on it.
-
I want to say thank you to you guys. This is the first time I buy dumps from you while I think I will be a regular customer.
-
today all the question are from this dumps, so i passed the exam without doubt. thanks for it. Recommend.
-
hi guys, thanks for your help. I passed the exam with good score yesterday. Thanks a million.
-
valid 100% thanks for helping me pass the exam.
-
Now, i'm very happy that i have passed the exam in the morning. Thanks for my friend introduce this good dumps to me. i will also recommend this good dumps to others.
-
Passed with 927/1000 yesterday.This dumps is valid. Thank you all !!!
-
Pass with score 964/1000, this dumps is valid. I think this dumps is enough for the exam, so you can trust on it.
-
this dumps is useful and convenient, i think it will be your best choice. believe on it .
-
This is the valid dumps. I passed mine yesterday. All the questions are from this dumps. Thanks.


 Printable PDF
Printable PDF