EC-Council Certified Computer Hacking Forensic Investigator (V8): 312-49V8
Want to pass your EC-Council Certified Computer Hacking Forensic Investigator (V8) 312-49V8 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: EC-COUNCIL
- Exam Code: 312-49V8
- Exam Name: EC-Council Certified Computer Hacking Forensic Investigator (V8)
- Certifications: EC-COUNCIL Certifications
- Total Questions: 180 Q&As
- Updated on: Mar 09, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
EC-COUNCIL 312-49V8 Last Month Results
Free 312-49V8 Exam Questions in PDF Format
Related EC-COUNCIL Certifications Exams
312-49V8 Online Practice Questions and Answers
Questions 1
Computer security logs contain information about the events occurring within an organization's systems and networks. Application and Web server log files are useful in detecting web attacks. The source, nature, and time of the attack can be determined by _________of the compromised system.
A. Analyzing log files
B. Analyzing SAM file
C. Analyzing rainbow tables
D. Analyzing hard disk boot records
Questions 2
Data is striped at a byte level across multiple drives and parity information is distributed among all member drives.
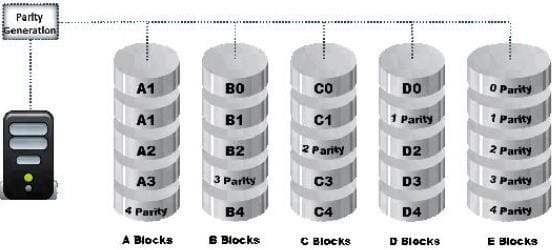
What RAID level is represented here?
A. RAID Level0
B. RAID Level 1
C. RAID Level 3
D. RAID Level 5
Questions 3
When the operating system marks cluster as used, but does not allocate them to any file, such clusters are known as ___________.
A. Lost clusters
B. Bad clusters
C. Empty clusters
D. Unused clusters
Reviews
-
passed today. I think it is very useful and enough for your exam, so trust on it and you will achieve success.
-
Now, i have finished my exam. I really appreciate for the help of this dumps. Thanks very much.
-
Hello, guys. i have passed the exam successfully in the morning,thanks you very much.
-
Great dumps! I have passed the exam by using this dumps only half a month. I will share with my friend.
-
Passed today with 938. There are a lot of D&D but only 3-4 new. Thank you all!
-
This dumps is still very valid, I have cleared the written exams passed today. Recommend.
-
Dumps are valid. I passed my exam this morning. Few questions are different with the Qs from the dumps but never mind. I passed. Thank you. Good luck to you all.
-
I only used this dumps and my book. I passed the exam with high score surprisingly. Really thanks for this valid dumps.
-
Passed today with 9xx. The dumps is more than enough. There are also the same new questions in the exam but I cannot remember. Sorry...
-
Valid, around 3 questions are different, d & g different as well,rest are fine


 Printable PDF
Printable PDF