Designing and Implementing Cloud Connectivity (ENCC): 300-440
Want to pass your Designing and Implementing Cloud Connectivity (ENCC) 300-440 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: Cisco
- Exam Code: 300-440
- Exam Name: Designing and Implementing Cloud Connectivity (ENCC)
- Certifications: CCNP Enterprise
- Total Questions: 38 Q&As( View Details)
- Updated on:
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
Cisco 300-440 Last Month Results
Free 300-440 Exam Questions in PDF Format
Related CCNP Enterprise Exams
300-440 Online Practice Questions and Answers
Questions 1
Which method is used to create authorization boundary diagrams (ABDs)?
A. identify only interconnected systems that are FedRAMP-authorized
B. show all networks in CIDR notation only
C. identify all tools as either external or internal to the boundary
D. show only minor or small upgrade level software components
Questions 2
Refer to the exhibit.
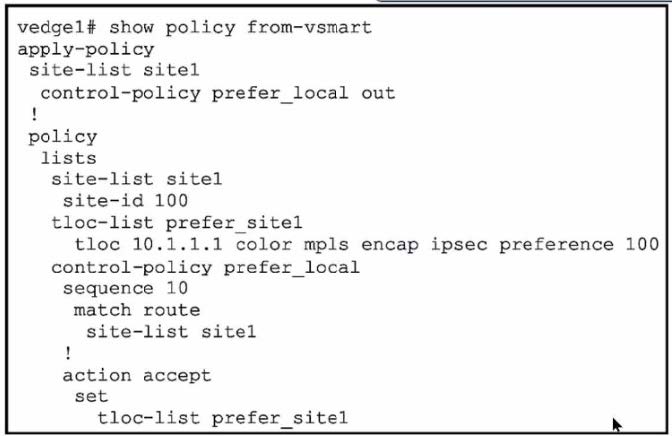
A network engineer discovers that the policy that is configured on an on-premises Cisco WAN edge router affects only the route tables of the specific devices that are listed in the site list. What is the problem?
A. An inbound policy must be applied.
B. The action must be set to deny
C. A localized data policy must be configured.
D. A centralized data policy must be configured
Questions 3
Refer to the exhibits.
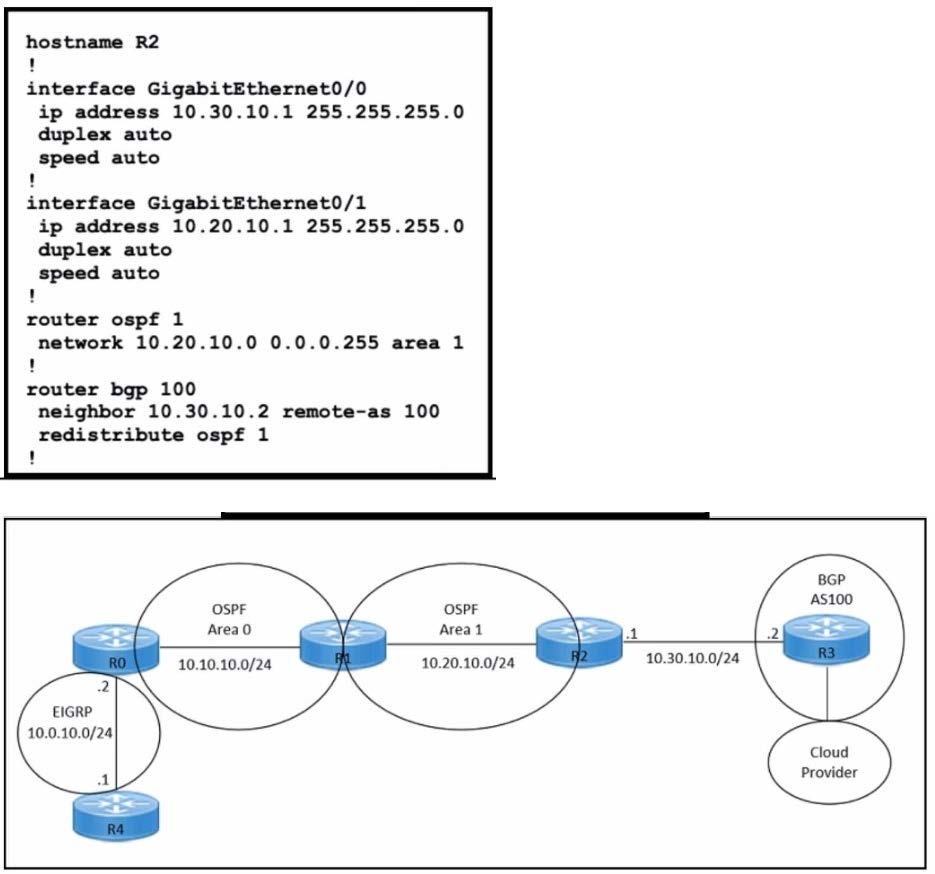
An engineer must redistribute only the 10.0.10.0/24 network into BGP to connect an on-premises network to a public cloud provider. These routes are currently redistributed:
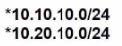
Which command is missing on router R2?
A. neighbor 10.0.10.2 remote-as 100
B. redistribute ospf 1 match internal
C. redistribute ospf 1 match external
D. neighbor 10.0.10.0/24 remote-as 100
Reviews
-
All this dumps are very good, i just did this one and took part in my exam. i really don't believe myself that i have got so high score. Thanks for their dumps.
-
valid just passed my exam with this dumps. SOme answers are incorrect. but so far so good. thanks
-
i have achieved high score by using this dumps good luck to you.
-
Valid today. Pass with this dumps. very good thanks a lot.
-
Pass with score 964/1000, this dumps is valid. I think this dumps is enough for the exam, so you can trust on it.
-
Nice study material, I passed the exam with the help of it. Recommend strongly.
-
Valid. All questions from the exam, few questions have the different order. So please be careful in the exam,
-
I pass my exam with a pretty score. The dumps are good and all the answers are correct. If you want to pass , you can use this dumps.
-
This is the best study material I have used ,and I will continue using it when I have exam. Believe me,you can trust on it.
-
This dumps is very very valid. I passed this week with a satisfied score. ALL questions were from this file.


 Printable PDF
Printable PDF