Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR): 300-215
Want to pass your Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR) 300-215 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: Cisco
- Exam Code: 300-215
- Exam Name: Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR)
- Certifications: CyberOps Professional
- Total Questions: 59 Q&As( View Details)
- Updated on: Feb 16, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
Cisco 300-215 Last Month Results
Free 300-215 Exam Questions in PDF Format
Related CyberOps Professional Exams
300-215 Online Practice Questions and Answers
Questions 1
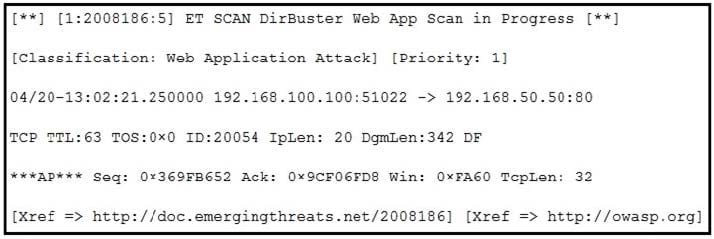
Refer to the exhibit. According to the SNORT alert, what is the attacker performing?
A. brute-force attack against the web application user accounts
B. XSS attack against the target webserver
C. brute-force attack against directories and files on the target webserver
D. SQL injection attack against the target webserver
Questions 2
A scanner detected a malware-infected file on an endpoint that is attempting to beacon to an external site. An analyst has reviewed the IPS and SIEM logs but is unable to identify the file's behavior. Which logs should be reviewed next to evaluate this file further?
A. email security appliance
B. DNS server
C. Antivirus solution
D. network device
Questions 3
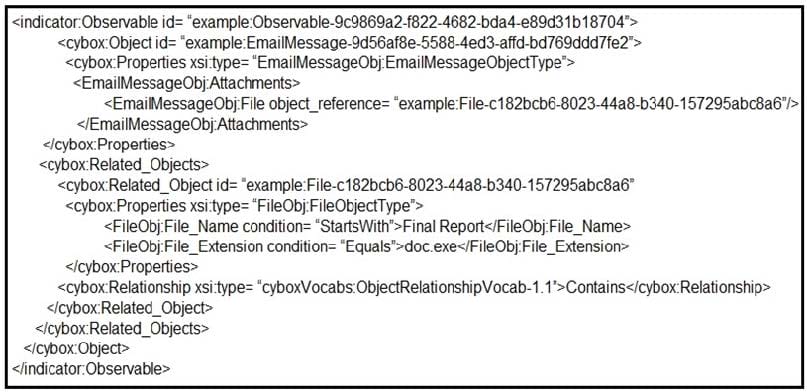
Refer to the exhibit. Which determination should be made by a security analyst?
A. An email was sent with an attachment named "Grades.doc.exe".
B. An email was sent with an attachment named "Grades.doc".
C. An email was sent with an attachment named "Final Report.doc".
D. An email was sent with an attachment named "Final Report.doc.exe".
Reviews
-
i really love this dumps, update quickly and content completely. it is enough for my exam. Recommend.
-
valid just passed my exam with this dumps. SOme answers are incorrect. but so far so good. thanks
-
Yes, i have passed the exam by using this dumps,so you also can try it and you will have unexpected achievements. Recommend to all.
-
Before attending the exam, I have studied every question and answer. when i seated for exam, I felt confident in every question. At last, I passed the exam with high score without doubt.Thanks for this valid dumps.
-
I pass today . In my opinion,this dumps is enough to pass exam. Good luck to you.
-
I studied this material carefully and took every question seriously. At last, I passed the exam with high score. Prepare well and study much more.
-
This is the valid dumps. I passed mine yesterday. All the questions are from this dumps. Thanks.
-
I just passed my exam by using this dumps, thanks to thier efforts which help to get the certificates in easy way.
-
This study material is very useful and effective, if you have not much time to prepare for your exam, this study material is your best choice.
-
Valid, around 3 questions are different, d & g different as well,rest are fine


 Printable PDF
Printable PDF