Architecting a Citrix Networking Solution: 1Y0-440
Want to pass your Architecting a Citrix Networking Solution 1Y0-440 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: Citrix
- Exam Code: 1Y0-440
- Exam Name: Architecting a Citrix Networking Solution
- Certifications: Citrix Certifications
- Total Questions: 63 Q&As( View Details)
- Updated on: Jan 29, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
Citrix 1Y0-440 Last Month Results
Free 1Y0-440 Exam Questions in PDF Format
Related Citrix Certifications Exams
1Y0-440 Online Practice Questions and Answers
Questions 1
Scenario: A Citrix Architect has implemented two high availability pairs of MPX 5500 and MPX 11500 devices respectively with 12.0.53.13 nc version. The NetScaler devices are set up to handle NetScaler Gateway, Load Balancing, Application Firewall, and Content Switching. The Workspacelab infrastructure is set up to be monitored with NMAS version 12.0.53.13 nc by the Workspacelab administrators. The Workspacelab team wants to implement one more pair of NetScaler MPX 7500 devices with version
12.0.53.13 nc.
The Citrix consulting team has assigned the task to implement these NetScaler devices in the infrastructure and set them up to be monitored and managed by NMAS.
The following are the requirements that were discussed during the project initiation call:
1.
NMAS should be configured to get the infrastructure information under sections such as HDX Insight, WEB Insight, and Security Insight.
2.
Configuration on the new MPX devices should be identical to MPX 11500 devices.
3.
Configuration changes after the deployment and initial setup should be optimized using NMAS.
4.
NMAS should be utilized to configure templates that can be utilized by the Workspacelab team in future deployment.
5.
As per the requirement from the Workspacelab team, NMAS should be store the audited data for only 15 days.
Which process should the architect utilize to ensure that the deployment of MPX 11500 devices are optimized and that it is correct, before deploying the devices in production?
A. Under Stylebooks; Inbuilt and composite stylebook templates should be utilized prior to deployment.
B. Under Stylebooks; Public and composite stylebook templates should be utilized prior to deployment.
C. Under Configuration Management; Configuration Audit and Advice should be used prior to deployment.
D. Under Configuration jobs; Configuration Audit and Advice should be used prior to deployment.
Questions 2
Scenario: A Citrix Architect and a team of Workspacelab members have met for a design discussion about the NetScaler Design Project. They captured the following requirements:
1.
Two pairs of NetScaler MPX appliances will be deployed in the DMZ network and the internal network.
2.
High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
3.
Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
4.
The NetScaler Gateway virtual server is integrated with XenApp/XenDesktop environment.
5.
Load balancing must be deployed for the users from the workspacelab.com and vendorlab.com
domains.
6.
The logon page must show the workspacelab logo.
7.
Certificate verification must be performed to identify and extract the username.
8.
The client certificate must have UserPrincipalName as a subject.
9.
All the managed workstations for the workspace users must have a client identifications certificate
installed on it.
10.The workspacelab users connecting from a managed workstation with a client certificate on it should be
authenticated using LDAP. 11.The workspacelab users connecting from a workstation without a client
certificate should be authenticated using LDAP and RADIUS.
12.The vendorlab users should be authenticated using Active Directory Federation Service.
13.The user credentials must NOT be shared between workspacelab and vendorlab.
14.Single Sign-on must be performed between StoreFront and NetScaler Gateway.
15.A domain drop down list must be provided if the user connects to the NetScaler Gateway virtual server
externally.
16.The domain of the user connecting externally must be identified using the domain selected from the
domain drop down list.
On performing the deployment, the architect observes that users are always prompted with two-factor authentication when trying to assess externally from an unmanaged workstation.
Click the exhibit button to view the configuration.
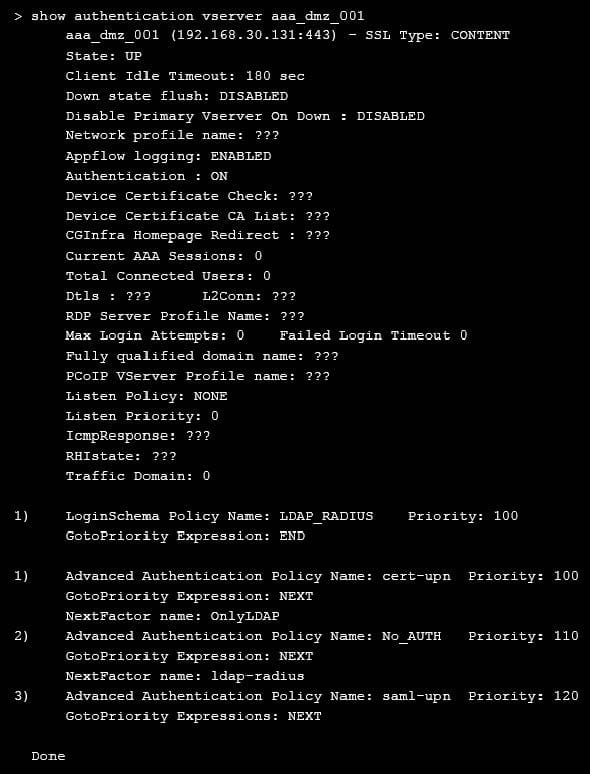
What should the architect do to correct this configuration?
A. Unbind LoginSchema Policy LDAP_RADIUS from the virtual server.
B. Bind the Portal theme as Domaindropdown.
C. Bind the LoginSchema Policy Domaindropdown to priority 90.
D. Bind the Default LoginSchema Policy as Domaindropdown.
Questions 3
Scenario: A Citrix Architect needs to assess an existing NetScaler configuration. The customer recently found that certain user groups were receiving access to an internal web server with an authorization configuration that does NOT align with the designed security requirements.
Click the Exhibit button view the configured authorization settings for the web server.
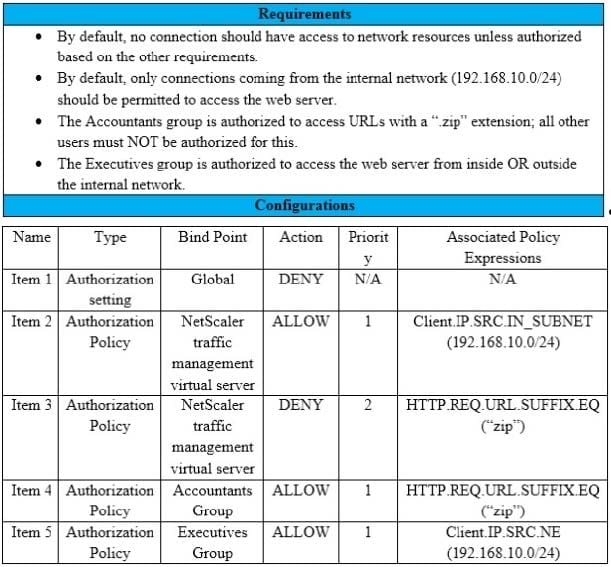
Which item should the architect change or remove to align the authorization configuration with the security requirements of the organization?
A. Item 1
B. Item 3
C. Item 4
D. Item 5
E. Item 2
Reviews
-
Very good dumps, take full use of it, you will pass the exam just like me.
-
this dumps is valid. All questions that I met in the exam are from this dumps !!!
-
This dumps is still very valid, I have cleared the written exams passed today. Recommend.
-
Many questions are from the dumps but few question changed. Need to be attention.
-
Valid dumps. Thanks very much.
-
hi guys i had exam yesterday and passed
It is really a good dumps.Thanks very much. -
took the exams yesterday and scored 9xx.dumps are valid. almost all of the multiple choice came out. I advice know ur material very well and then U can read dumps. good success
-
Very good study material, I just passed my exam with the help of it. Good luck to you.
-
Yes this valid. Passed today 982/1000. Same questions.
-
Do not reply on a dumps to pass the exam.
Utilize GNS3 or real equipment to learn the technology.
Please do not degrade the value of this Cisco Cert.


 Printable PDF
Printable PDF