CIW v5 Security Essentials: 1D0-571
Want to pass your CIW v5 Security Essentials 1D0-571 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: CIW
- Exam Code: 1D0-571
- Exam Name: CIW v5 Security Essentials
- Certifications: CIW Certifications
- Total Questions: 62 Q&As
- Updated on: Feb 16, 2025
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
CIW 1D0-571 Last Month Results
Free 1D0-571 Exam Questions in PDF Format
Related CIW Certifications Exams
1D0-571 Online Practice Questions and Answers
Questions 1
You are creating an information security policy for your company. Which of the following activities will help you focus on creating policies for the most important resources?
A. Auditing the firewall
B. Implementing non-repudiation
C. Logging users
D. Classifying systems
Questions 2
Consider the following image of a packet capture: This packet capture has recorded two types of attacks. Which choice lists both attack types?
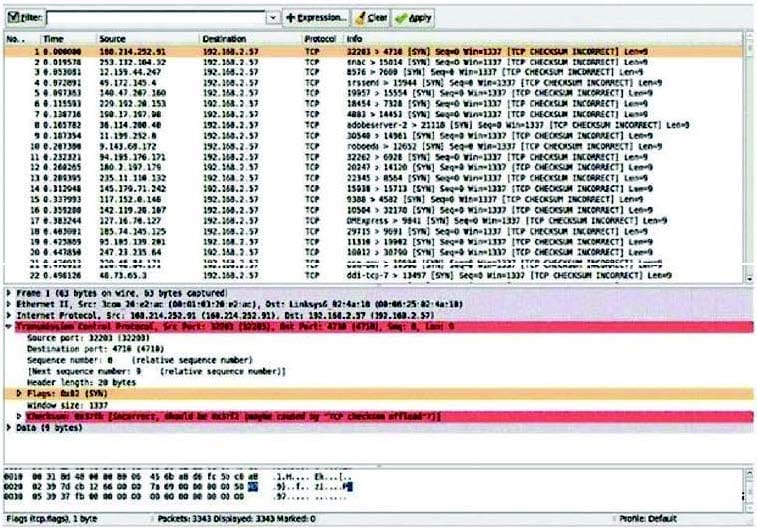
A. A dictionary attack and a worm-basedattackA.A dictionary attack and a worm-based attack
B. Asyn flood attack and a spoofing attackB.A syn flood attack and a spoofing attack
C. A worm attack and abotnet attack C.A worm attack and a botnet attack
D. A SQL injection attack and a virusattackD.A SQL injection attack and a virus attack
Questions 3
Consider the following image of a packet capture:
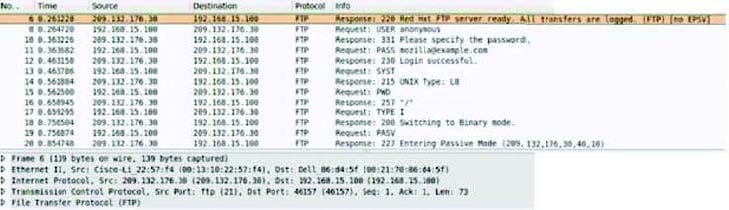
Which of the following best describes the protocol used, along with its primary benefit?
A. It is a passive FTP session, which is easier for firewalls to process.
B. It is an active FTP session, which is necessary in order to support IPv6.
C. It is an extended passive FTP session, which is necessary to support IPv6.
D. It is an active FTP session, which is supported by all FTP clients.
Reviews
-
I passed the exam today. This dumps is valid and enough to your exam. I will share with my friends.
-
I pass today, The dumps is good. 90% questions are from this dumps. so it is enough for the exam as long as you study this dumps carefully and do the all questions especially the new questions.
-
Thanks for my friend's introduction, I passed the exam by using this study material luckily. Good lucky to you!
-
hi guys , i passed this exam today. Really thanks for this dumps,Recommend strongly.
-
Test engine works fine. Pass my exam. Thank you.
-
thank God . i passed my exams. This dumps is 100% valid so try to learn how to subnet very vell . wish u all the best in ur exams
-
One of my friends told me that your dumps are good and I purchased it. Great. I passed my exam with it. Nice work, guys.
-
I just passed my exam by using this dumps, thanks to thier efforts which help to get the certificates in easy way.
-
About 3 questions are different, but the remaining is ok for pass. I passed successfully.
-
Yeah , Get 869/1000 score, this dumps still valid 100% but the some os answer is not correct.


 Printable PDF
Printable PDF