Accelerated CCSE NGX R65: 156-915.65
Want to pass your Accelerated CCSE NGX R65 156-915.65 exam in the very first attempt? Try Pass2lead! It is equally effective for both starters and IT professionals.
- Vendor: CheckPoint
- Exam Code: 156-915.65
- Exam Name: Accelerated CCSE NGX R65
- Certifications: CheckPoint Certification
- Total Questions: 204 Q&As
- Updated on: Dec 18, 2024
- Note: Product instant download. Please sign in and click My account to download your product.

- Q&As Identical to the VCE Product
- Windows, Mac, Linux, Mobile Phone
- Printable PDF without Watermark
- Instant Download Access
- Download Free PDF Demo
- Includes 365 Days of Free Updates

VCE
- Q&As Identical to the PDF Product
- Windows Only
- Simulates a Real Exam Environment
- Review Test History and Performance
- Instant Download Access
- Includes 365 Days of Free Updates
Passing Certification Exams Made Easy
Everything you need prepare and quickly pass the tough certification exams the first time
- 99.5% pass rate
- 7 Years experience
- 7000+ IT Exam Q&As
- 70000+ satisfied customers
- 365 days Free Update
- 3 days of preparation before your test
- 100% Safe shopping experience
- 24/7 Support
CheckPoint 156-915.65 Last Month Results
Free 156-915.65 Exam Questions in PDF Format
Related CheckPoint Certification Exams
156-915.65 Online Practice Questions and Answers
Questions 1
What must a public hospital Security Administrator do to comply with new health-care legislation requirements for logging all traffic accepted through the perimeter Security Gateway?
A. Define two log servers on the VPN-1 NGX R65 Gateway object. Enable "Log Implied Rules" on the first log server. Enable "Log Rule Base" on the second log server. Use Eventia Reporter to merge the two log server records into the same database for HIPPA log audits.
B. Install the "View Implicit Rules" package using SmartUpdate.
C. In Global Properties > Reporting Tools check the box "Enable tracking all rules (including rules marked as 'None' in the Track column). Send these logs to a secondary log server for a complete logging history Use your normal log server for standard logging for troubleshooting.
D. Check the "Log Implied Rules Globally" box on the VPN-1 NGX R65 Gateway object.
Questions 2
An NGXR65 HA cluster contains two members with external interfaces 172.28.108.1 and 172.28.108.2. The internal interfaces are 10.4.8.1 and 10.4.8.2. The external cluster VIP address is 172.28.108.3 and the internal cluster VIP address is 10.4.8.3. The synchronization interfaces are 192.168.1.1 and 192.168.1.2. The Security Administrator discovers State Synchronization is not working properly. The cphaprob if command output displays shows:What is causing the State Synchronization problem?
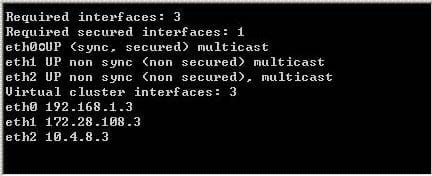
A. The synchronization network has been defined as "Network Objective: Cluster + 1st sync" with an IP address 192.168.1.3 defined in the NGX cluster object's topology. This configuration is supported in NGX and therefore the above screenshot is not relevant to the sync problem.
B. The synchronization interface on the individual NGX cluster member object's Topology tab is enabled with "Cluster Interface". Disable this setting.
C. The synchronization network has a cluster VIP address (192.168.1.3) defined in the NGX cluster object's topology. Remove the 192.168.1.3 VIP interface from the cluster topology.
D. Another cluster is using 192.168.1.3 as one of the unprotected interfaces.
Questions 3
A security audit has determined that your unpatched web application server is revealing the fact that it accesses a SQL server. You believe that you have enabled the proper SmartDefense setting but would like to verily this fact using SmartView Tracker. Which of the following entries confirms the proper blocking of this leaked information to an attacker?
A. "Fingerprint Scrambling: Changed [SQL] to [Perl]"
B. "HTTP response spoofing: remove signature [SQL Server]"
C. "Concealed HTTP response [SQL Server]. (Error Code WSE0160003)"
D. "ASCII Only Response Header detected: SQL"
Reviews
-
I passed the exam with perfect score. I'm so happy now. Thanks for my friends introduction, thanks for this dumps.
-
Valid dumps. Thanks very much.
-
Passed my exam today. Great job.Thanks this dumps.
-
Thanks for the help of this dumps, i achieved the full score in the exam. I will share this dumps with my good friends.
-
i cannot image that i would pass the exam with so high score, thanks for this dumps. Recommend.
-
Great dumps ! Thanks a million.
-
This dumps is very valid, and i have passed the exam perfectly. Thanks very much, I will continue using it.
-
This is latest Dumps and all the answers are accurate. You can trust on this. Recommend.
-
Yeah , Get 869/1000 score, this dumps still valid 100% but the some os answer is not correct.
-
Valid dumps. Answers are accurate. I come get few new questions in the exam. Maybe 2-3 VERY SIMPLE. Good Luck All!!!!


 Printable PDF
Printable PDF